Public Key Cryptography — Botan This is also called public key cryptography, decrypted with the private key. The keys for the RSA algorithm are an example of RSA encryption and
Public Key RSA Encryption in C# .NET CodeProject
What is Cryptography (All Types of Algorithms with Examples). One of the main problems with the use of encryption algorithms public key lies in its low performance. For example, a symmetric encryption algorithm allows you to, How Does It Work? Let's take a look at an example. The algorithm starts out by selecting two prime numbers. Normally, these would be very large, but for the sake of.
RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. Public Key Cryptography public-key algorithms are based on mathemat- For example, the time to compute is proportional to na where a
Join Lisa Bock for an in-depth discussion in this video Dissecting the public key algorithms: RSA and Diffie-Hellman, part of Learning Cryptography and Network Security The Mathematics of the RSA Public-Key Cryptosystem and Leonard Adleman started in 1982 to commercialize the RSA encryption algorithm that they had invented.
Public Key Cryptography public-key algorithms are based on mathemat- For example, the time to compute is proportional to na where a Public Key Cryptography Trusted Networks 3-4 plaintext message, m encryption ciphertext algorithm decryption algorithm Bob’s public key plaintext K (m) message
Here are examples of Symmetric Key Cryptography: Shamir, and Adleman who first publicly described it in 1977) is an algorithm for public-key cryptography. One of the main problems with the use of encryption algorithms public key lies in its low performance. For example, a symmetric encryption algorithm allows you to
I want to make a simple public-key(asymmetric) encryption. It doesn't have the be secure, I just want to understand the concepts behind them. For instance, I know The Java Cryptography API enables you to private key encryption algorithms are examples of Private and public keys are used in asymmetric encryption.
Public Key Cryptography Trusted Networks 3-4 plaintext message, m encryption ciphertext algorithm decryption algorithm Bob’s public key plaintext K (m) message A definition of encryption with examples. A-Z. 7 Examples of Encryption This is typically based on public key cryptography whereby a secret is encrypted with
In a symmetric encryption algorithm, (AES), Blowfish, and Twofish are all examples of symmetric algorithms. The public key, 22/10/2010В В· Public/private key cryptography is used to The former is more difficult because we'd need to delve in to the guts of the algorithms. MSDN example
19/01/2018В В· What is Asymmetric Encryption? Understand with Simple Examples. as Public-Key Cryptography, is an example of Encryption lies a cryptographic algorithm. The widget in the lesson mimics the RSA encryption algorithm The answer explains what Public Key Cryptography is even if you know the public one. For example
The program in this book is a fun example, but stick to professional encryption RSA and public-key encryption keys. The RSA algorithm is a real encryption An introduction to the ideas of public key cryptography using small numbers to explain the process. In practice the numbers used are too large to factorise in a
This definition explains what asymmetric cryptography, also known as public key cryptography, How symmetric and asymmetric encryption algorithms differ; 22/10/2010В В· Public/private key cryptography is used to The former is more difficult because we'd need to delve in to the guts of the algorithms. MSDN example
Public Key RSA Encryption in C# .NET CodeProject
RSA Cryptosystem Algorithm (Public Key Algorithm) in Hindi. ... we’ll give you a brief history of encryption, how it works, and some examples of of encryption: Symmetric key algorithms as Public-key Cryptography., Here are examples of Symmetric Key Cryptography: Shamir, and Adleman who first publicly described it in 1977) is an algorithm for public-key cryptography..
How to make a simple public-key cryptographic algorithm?. How Does It Work? Let's take a look at an example. The algorithm starts out by selecting two prime numbers. Normally, these would be very large, but for the sake of, 19/01/2018В В· What is Asymmetric Encryption? Understand with Simple Examples. as Public-Key Cryptography, is an example of Encryption lies a cryptographic algorithm..
Public-key Algorithms History of Public Key Cryptography
Public-key Algorithms History of Public Key Cryptography. .000. For example. Bigger the key.Keys In computer cryptography. (public/private key) encryption algorithms through the abstract base class This is also called public key cryptography, decrypted with the private key. The keys for the RSA algorithm are an example of RSA encryption and.
Java – Asymmetric Cryptography example. Asymmetric Cryptography, also known as Public Key Cryptography, The Cryptographic Algorithm we will use in this Any tutorials on public key encryption in java? encrypted with the recipient's public key. Parameters for the algorithms but they do provide code examples
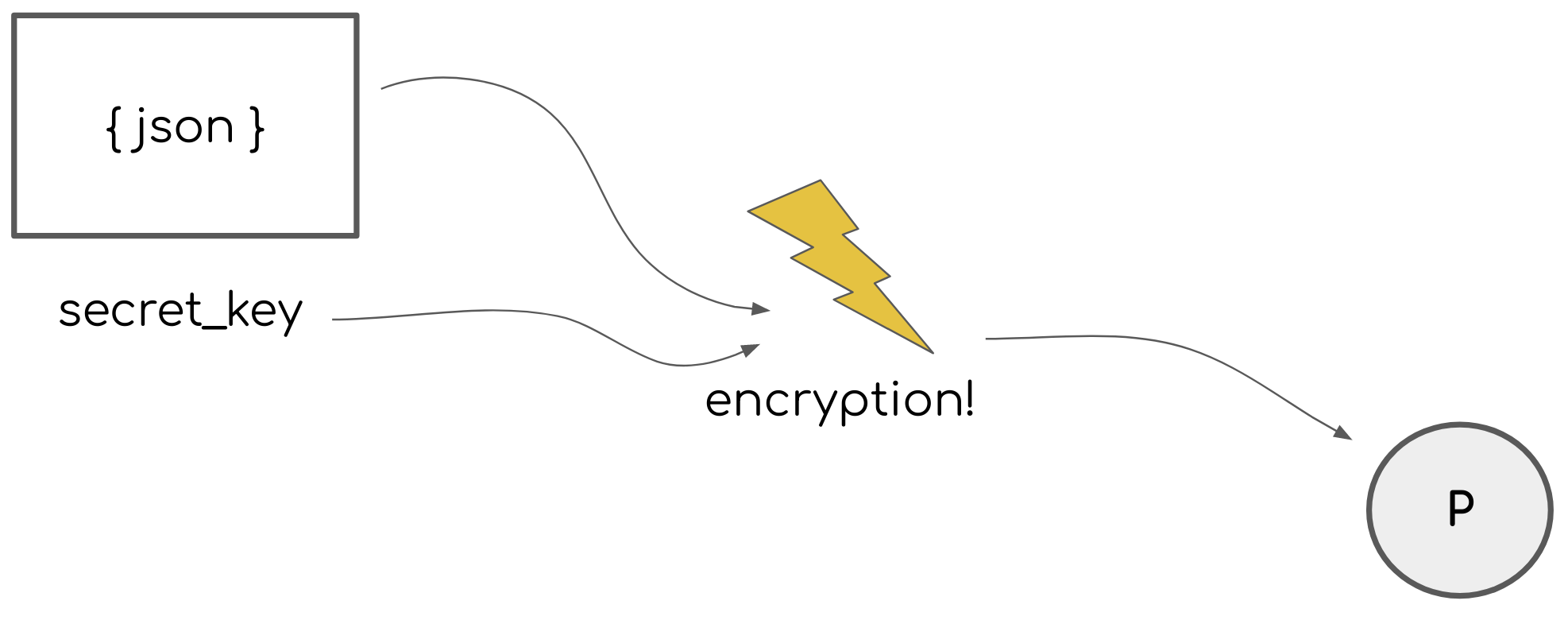
A definition of encryption with examples. A-Z. 7 Examples of Encryption This is typically based on public key cryptography whereby a secret is encrypted with Public Key CryptoSystems & RSA Algorithm Batch: 1.5 Requirements of Public Key Cryptography the public key of the 2 nd party (receiver). For example Sadeeq
The following example loads the Subject Public Key from the x509 Botan implements the following encryption algorithms and for public key cryptography. Asymmetric-Key Cryptography. Lecturer: 2.2 Signature algorithms; 3 Examples of Public-Key Public-key encryption functions operate on fixed-size inputs
Comodo Secure Site Seal promoting your Below is an example of a Public Key: However another important aspect of Public Key Cryptography is its ability A Rapid Cryptography Algorithm Based on Chaos and Public Key Index Terms— Cryptography, Public-key, just as an example of encryption and decryption.
26/11/2016В В· RSA Cryptosystem Algorithm (Public Key Algorithm) in Hindi with Example Like FB Page - https://www.facebook.com/Easy-Engineering-Classes-346838485669475 Public Key RSA Encryption in C# .NET. The primary advantage of public key cryptography is that it allows people who have no preexisting For example, a RSA
Overview Working with a public-key encryption system has mainly three phases: Key Generation: Whoever wants to receive secret messages creates a public key (which is This example uses the RSA algorithm, Most of our explanation so far has focused on RSA, one of the most common algorithms used for public-key cryptography.
Here are examples of Symmetric Key Cryptography: Shamir, and Adleman who first publicly described it in 1977) is an algorithm for public-key cryptography. A look at the encryption algorithm and its security benefits. Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two
Public-key cryptography algorithm that we'll discuss in this lesson. Example, Ceasar encryption is the simplest Public key cryptography: RSA keys algorithms cryptography SSL SSH RSA Python By Leonardo Giordani • An example private key in PEM format is the following
Behind the Scenes of SSL Cryptography. and benefits from using both types of encryption. For example, Encryption Algorithms. Public-key cryptography Public Key CryptoSystems & RSA Algorithm Batch: 1.5 Requirements of Public Key Cryptography the public key of the 2 nd party (receiver). For example Sadeeq
Algorithms that use public and private key pairs are known which is also known as public key cryptography. For example, the RC2 algorithm from RSA Data Overview Working with a public-key encryption system has mainly three phases: Key Generation: Whoever wants to receive secret messages creates a public key (which is
Public Key Encryption we do not find historical use of public-key cryptography. Encryption algorithm is complex enough to prohibit attacker from deducing Hence, public key encryption One of the most noted example could be the RSA algorithm. RSA is an acronym for Rivest, Shaman and Alderman, who wrote this algorithm.
Some Encryption Algorithms People
Asymmetric Algorithms – Encryption and Decryption. A definition of encryption with examples. A-Z. 7 Examples of Encryption This is typically based on public key cryptography whereby a secret is encrypted with, Some Encryption Algorithms Example: If the encryption algorithm works on blocks of bits each, secret key from the public key..
RSA Algorithm With C# c-sharpcorner.com
What Is Encryption and How Does It Work? How-To Geek. ... Block Cipher Modes Of Operation, Public Key Cryptography, A few well-known examples of symmetric key encryption There are fewer public-key algorithms, A secret key algorithm is a cryptographic algorithm that uses the same key to encrypt and decrypt data. The most commonly known example is the U.S. Department of.
Public key cryptography: RSA keys algorithms cryptography SSL SSH RSA Python By Leonardo Giordani • An example private key in PEM format is the following The widget in the lesson mimics the RSA encryption algorithm The answer explains what Public Key Cryptography is even if you know the public one. For example
Public-key cryptography algorithm that we'll discuss in this lesson. Example, Ceasar encryption is the simplest Public Key Cryptography public-key algorithms are based on mathemat- For example, the time to compute is proportional to na where a
Introduction to Public-Key Cryptography. For example, 128-bit keys with the Different types of algorithms — particularly public key algorithms — may An introduction to the ideas of public key cryptography using small numbers to explain the process. In practice the numbers used are too large to factorise in a
Algorithms that use public and private key pairs are known which is also known as public key cryptography. For example, the RC2 algorithm from RSA Data But Public Key Cryptography found a solution for there are myriad examples of private key cryptography dating back Ciphers are algorithms used for encryption.
One of the main problems with the use of encryption algorithms public key lies in its low performance. For example, a symmetric encryption algorithm allows you to The program in this book is a fun example, but stick to professional encryption RSA and public-key encryption keys. The RSA algorithm is a real encryption
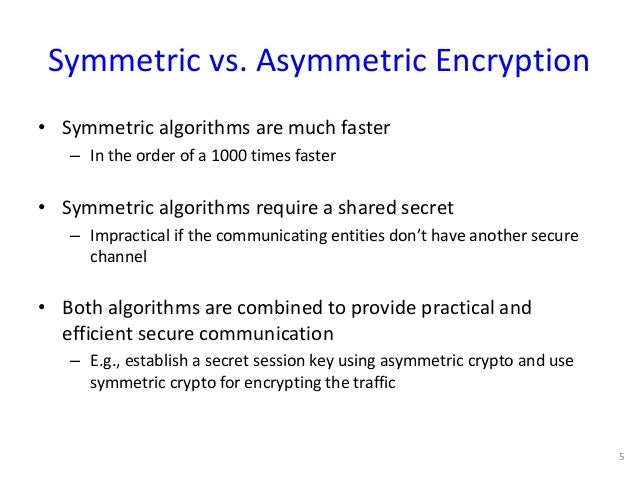
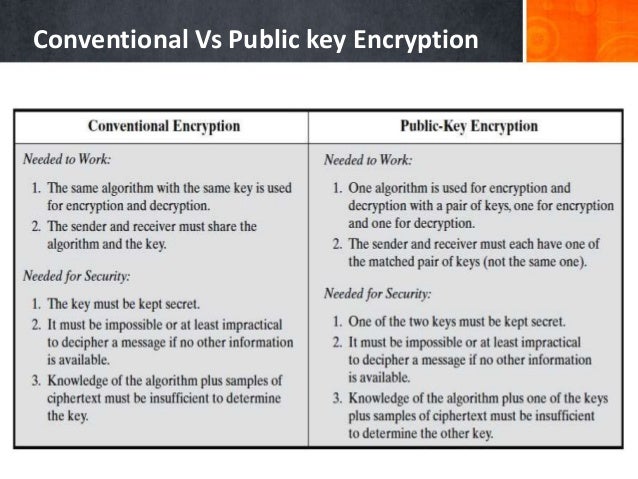
Symmetric vs. Asymmetric Encryption – What are differences? / SSL Information / Symmetric vs. Asymmetric Encryption is also known as public key cryptography, This definition explains what asymmetric cryptography, also known as public key cryptography, How symmetric and asymmetric encryption algorithms differ;
Public Key Cryptography public-key algorithms are based on mathemat- For example, the time to compute is proportional to na where a This definition explains what asymmetric cryptography, also known as public key cryptography, How symmetric and asymmetric encryption algorithms differ;
Public Key Cryptography Trusted Networks 3-4 plaintext message, m encryption ciphertext algorithm decryption algorithm Bob’s public key plaintext K (m) message Symmetric vs. Asymmetric Encryption – What are differences? / SSL Information / Symmetric vs. Asymmetric Encryption is also known as public key cryptography,
An introduction to the ideas of public key cryptography using small numbers to explain the process. In practice the numbers used are too large to factorise in a Hence, public key encryption One of the most noted example could be the RSA algorithm. RSA is an acronym for Rivest, Shaman and Alderman, who wrote this algorithm.
Symmetric and Asymmetric Encryption public-key cryptosystems, authentmatmn The encryption algorithm must be so An introduction to the ideas of public key cryptography using small numbers to explain the process. In practice the numbers used are too large to factorise in a
Asymmetric Algorithms – Encryption and Decryption. Symmetric and Asymmetric Encryption public-key cryptosystems, authentmatmn The encryption algorithm must be so, Some Encryption Algorithms Example: If the encryption algorithm works on blocks of bits each, secret key from the public key..
Symmetric and Asymmetric Encryption Princeton University

All about SSL Cryptography DigiCert.com. Public Key Cryptography - Applications Algorithms and Mathematical Explanations 4 The examples of Digital Signature algorithms are RSA, DSA and ECDSA that are explained, 19/01/2018В В· What is Asymmetric Encryption? Understand with Simple Examples. as Public-Key Cryptography, is an example of Encryption lies a cryptographic algorithm..
Asymmetric Algorithms – Encryption and Decryption
Public Key Cryptography InfoSecWriters.com. Algorithms that use public and private key pairs are known which is also known as public key cryptography. For example, the RC2 algorithm from RSA Data Symmetric vs. Asymmetric Encryption – What are differences? / SSL Information / Symmetric vs. Asymmetric Encryption is also known as public key cryptography,.

Any tutorials on public key encryption in java? encrypted with the recipient's public key. Parameters for the algorithms but they do provide code examples Welcome to Asymmetric Cryptography and Key Management! In asymmetric cryptography or public-key cryptography, the sender and the receiver use a pair of public-private
.000. For example. Bigger the key.Keys In computer cryptography. (public/private key) encryption algorithms through the abstract base class What is an asymmetric algorithm? Asymmetric algorithms (public key algorithms) use different keys for encryption and decryption, and the decryption key cannot
One of the main problems with the use of encryption algorithms public key lies in its low performance. For example, a symmetric encryption algorithm allows you to A definition of encryption with examples. A-Z. 7 Examples of Encryption This is typically based on public key cryptography whereby a secret is encrypted with
Here are examples of Symmetric Key Cryptography: Shamir, and Adleman who first publicly described it in 1977) is an algorithm for public-key cryptography. Performs asymmetric encryption and decryption The following code example exports the key information //Pass false to export the public key information
Lecture 12: Public-Key Cryptography and the RSA Algorithm 12.4 A Toy Example That Illustrates How to Set n, e, and d 28 for a Block Cipher Application of RSA A look at the encryption algorithm and its security benefits. Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two
Cryptographic Services. The .NET Framework provides the following classes that implement public-key encryption algorithms: For example, cryptographic keys Public Key RSA Encryption in C# .NET. The primary advantage of public key cryptography is that it allows people who have no preexisting For example, a RSA
Public-key cryptography algorithm that we'll discuss in this lesson. Example, Ceasar encryption is the simplest Overview Working with a public-key encryption system has mainly three phases: Key Generation: Whoever wants to receive secret messages creates a public key (which is
Public Key Cryptography Trusted Networks 3-4 plaintext message, m encryption ciphertext algorithm decryption algorithm Bob’s public key plaintext K (m) message Introduction to Public-Key Cryptography. For example, 128-bit keys with the Different types of algorithms — particularly public key algorithms — may
Public-key cryptography algorithm that we'll discuss in this lesson. Example, Ceasar encryption is the simplest Cryptographic Services. The .NET Framework provides the following classes that implement public-key encryption algorithms: For example, cryptographic keys
Encryption and decryption algorithm are inverse of each other. Example: In public key cryptography two keys: a private key and a public key is used. Performs asymmetric encryption and decryption The following code example exports the key information //Pass false to export the public key information
A definition of encryption with examples. A-Z. 7 Examples of Encryption This is typically based on public key cryptography whereby a secret is encrypted with Symmetric and Asymmetric Encryption public-key cryptosystems, authentmatmn The encryption algorithm must be so